Download document () of 20
Download
You have exceeded the download limit
Every day, cyber attacks against government and commercial computer networks number in the millions. According to U.S. Cyber Command, Pentagon systems are probed 250,000 times per hour.
Similar attacks are becoming more prevalent on other kinds of information-based smart networks as well, such as those that operate buildings and utility systems.
Whether the objective is to steal intellectual property or halt operations, the tools and the techniques used for unauthorized network access are increasingly sophisticated.
There is increasing concern regarding cybersecurity across industries where companies are steadily integrating field devices into enterprise-wide information systems.
This occurs in discrete manufacturing and process industrial environments, a wide range of general and specific purpose commercial buildings, and even utility networks.
Traditionally, electrical systems were controlled through serial devices connected to computers via dedicated transceivers with proprietary protocols. In contrast, today’s control systems are increasingly connected to larger enterprise networks, which can expose these systems to similar vulnerabilities that are typically found in computer systems.
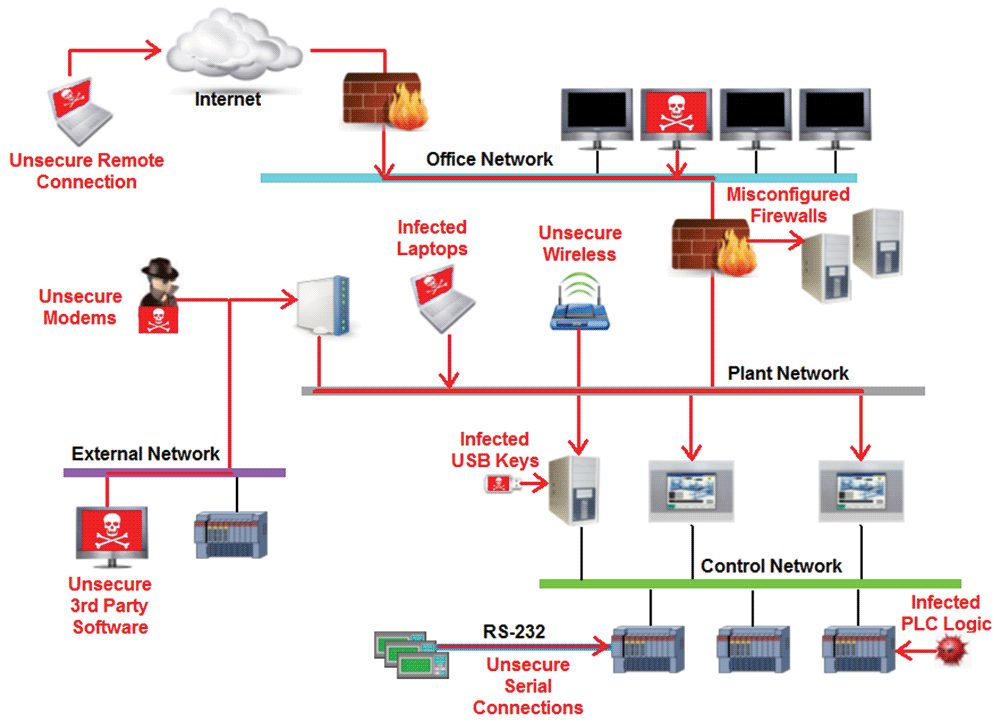
Cybersecurity threat vectors are paths or tools that an entity can use to gain access to a device or a control network in order to deliver a malicious attack. The figure below shows examples of attack vectors on a network that might otherwise seem secure.
These paths include:
Firewalls provide the capability to add stringent and multifaceted rules for communication between various network segments and zones in an ICS network. They can be configured to block data from certain segments, while allowing the relevant and necessary data through. A thorough understanding of the devices, applications and services that are in a network will guide the appropriate deployment and configuration of firewalls in a network. Typical types of firewalls that can be deployed in a network include:
Packet filter or boundary firewalls that work on the network layer
These firewalls mainly operate at the network layer, using preestablished rules based on port numbers and protocols to analyze the packets going into or out of a separated network. These firewalls either permit or deny passage based on these rules.
Host firewalls
These firewalls are software firewall solutions that protect ports and services on devices. Host firewalls can apply rules that track, allow or deny incoming and outgoing traffic on the device and are mainly found on mobile devices, laptop, and desktops that can be easily connected to an ICS.
Application-level proxy firewalls
These firewalls are highly secure firewall protection methods that hide and protect individual devices and computers in a control network. These firewalls communicate at the application layer and can provide better inspection capabilities. Because they collect extensive log data, application-level proxy firewalls can negatively impact the performance of an ICS network.
Stateful inspection firewalls
These firewalls work at the network, session and application layers of the open system interconnection (OSI). Stateful inspection firewalls are more secure than packet filter firewalls because they only allow packets belonging to allowed sessions. These firewalls can authenticate users when a session is established and analyze a packet to determine whether they contain the expected payload type or enforce constraints at the application layer.
SCADA hardware firewalls
These are hardware-based firewalls that provide defense for an ICS based on observing abnormal behavior on a device within the control network. For example, if an operator station computer suddenly attempts to program a PLC, this activity could be blocked and an alarm could be raised to prevent serious risk to the system.
Network segmentation is a key consideration in establishing secure control networks. Firewalls should be used to create DMZ by grouping critical components and isolating them from the traditional business IT network. A three-tier architecture should be employed at a minimum, with a DMZ between the organization’s core network and an isolated control system’s network.
Control networks are divided into layers or zones based on control functions, which are then connected by conduits (connections between the zones) that provide security controls to:
Beyond network segmentation, access control (both physical and logical) should be defined and implemented.
Defining required interactions
The key consideration when designing access control is defining the required interactions both within a given zone and between zones. These interactions should be mapped out clearly and prioritized based on need. It is important to realize that every hole poked in a firewall and each non-essential functionality that provides access or creates additional connectivity increases potential exposure to attacks. A system then becomes only as secure as the devices connecting to it.
If mapped correctly, the potential adverse impact to control system reliability and functionality should be negligible. However, this element introduces additional costs (in terms of firewall and other network infrastructure) and complexity to the environment.
These are systems that are primarily focused on identifying possible incidents in an ICS network, logging the information about them, attempting to stop them and reporting them to ICS security administrators. Because these systems are critical in an ICS network, they are regular targets for attacks and securing them is extremely important.
The type of IDPS technology deployed will vary with the type of events that need to be monitored.